![]() Introduction
Introduction
The communications model utilised directly impacts the device certificate and LFDI generation requirements for connecting to the Utility Server. This section outlines the certificate and LFDI generation requirements for different communication models.
For OEM interoperability testing, CPPALUE will act as the only SERCA and MICA/MCA will directly provision and share test certificates to OEMs for all Non-Production environments.
The certificate provisioning and management process will be different for our Production Minimum Demand LV DERMS system, as direct device OEMs will be offered the capability to provision their own MICA and device certificates.
Production system onboarding details and processes will be shared to OEMs once they have completed onboarding and interoperability testing.
The following certificate paths are accepted:
• SERCA> Device Certificate
• SERCA > MICA > Device Certificate
• SERCA > MCA > MICA > Device Certificate
All certificate files must include the full certificate chain of trust. Refer to Figure 8. For example, end device certificate file.

Figure 9: Example End Device Certificate File
![]() Requesting a Certificate
Requesting a Certificate
To request a Certificate, you must generate a private key and Certificate Signing Request (CSR). Once you have generated a private key and CSR, please email the CSR to OEM_Onboarding@powercor.com.au as part of the Application process. As CPPALUE will not be provisioning MICAs for Non-Production systems, the CSR generation process should be the same for both Aggregator and Direct device OEMs.
Refer to Appendix C: for CSR generation tips.
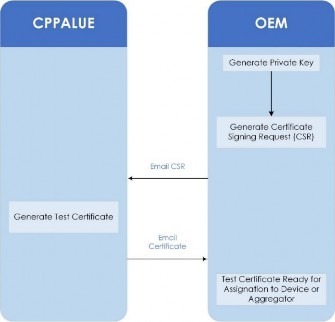
Figure 10: Requesting a Test Certificate
![]() Direct Device and Aggregator LFDIs
Direct Device and Aggregator LFDIs
LFDIs for direct connected devices and for aggregator instances must be generated as a hash of the device’s X.509 certificate. It must adhere to the following formatting specifications:
• Character set: Hexadecimal characters only (0-9, A-F)
• Length: 40 characters
The LFDI for a given device certificate can be generated with the following openssl command:
1. openssl x509 -outform der -in client-cert.pem | sha256sum | head -c 40 | tr '[a-f]' '[A-F]'
Alternatively, the LFDI for a given device certificate can be generated with the following PowerShell commands:
1. openssl x509 -outform der -in client-cert.pem -out client-cert.der
2. Get-FileHash client-cert.der
![]() Aggregator/Intermediary Software Client LFDIs
Aggregator/Intermediary Software Client LFDIs
Aggregators and software clients can represent multiple downstream sites or devices while communicating to the Utility Server as a single communicating client. These aggregators require a single certificate regardless of how many downstream devices it might represent. However, all downstream devices require their own LFDI to identify each site.
These downstream devices LFDIs shall be generated by the aggregator using the aggregator manufacturer’s Private Enterprise Number (PEN). The PEN shall be used as the last 8 digits of the LFDI with leading zeroes.
If your organisation does not have a PEN, you can request on for free from IANA. Aggregator Mediated Device LFDIs must adhere to the following formatting specifications:
• Character set: Hexadecimal characters only (0-9, A-F)
• Length: 40 characters
An example LFDI is as follows where [1234] is the PEN:
4B1AFA32312D2AA600ACF57E76FEBEDA00001234